Azure DevOps PipelinesとScanローカルエンジンの連携
Azure DevOps Pipelinesのプラグインを使用すると、Azure DevOps Pipelinesで直接、安全にオフラインで静的アプリケーションセキュリティテスト(SAST)を実行できます。ソースコードをビルド環境外に送信することなく、ローカルでスキャンを実行できます。このプラグインにより、スキャン処理の自動化、SARIF準拠レポートの作成、カスタマイズ可能なセキュリティしきい値の設定が可能になり、開発ライフサイクルの早い段階で脆弱性を特定できます。その際に、ソースコードへのアクセス権は完全に維持できます。
機能
開発パイプラインで静的スキャンを実行することにより、セキュリティの問題を早期に検出できます。
既存のAzure DevOpsプロジェクトとリポジトリでシームレスに連携し、ビルドパイプラインとリリースパイプラインの両方にタスクを追加できます。
デフォルトブランチのソースコードに対してローカルでSASTスキャンが実行され、ソースコードはビルド環境内に留まります。
パイプライン実行中にContrastからスキャナが自動的にダウンロードされます。
スキャン結果をContrastにアップロードすることで、結果が一元的に可視化され、修復状況を追跡できます。
アップロードされるファイルには、スキャンSARIFファイルにある全ての脆弱性の情報が含まれます。例えば、
Contrastが使用するスキャナに関する情報
スキャン対象とスキャン構成に関するデータ
脆弱性の検出結果に関するデータ
スキャン中に適切に処理されたエラーや通知内容
スキャンのカバレッジ情報
カスタマイズ可能な脆弱性検証:スキャン結果に基づき、設定可能な検証ロジックでパイプラインの合否判定を制御できます。
新規脆弱性の検証と深刻度による検証のモードに対応:
新規の検証:現在のスキャンを前回の結果と比較することで、新たに発生した脆弱性のみを検証します。新たな脆弱性が検出されると、その深刻度に関係なく、パイプラインは失敗します。この方法には、比較のために前回のスキャン結果が必要です。
深刻度の検証:しきい値として深刻度を定義できます(例、中など)。スキャンでは、選択した深刻度と一致するか、それを超える全ての脆弱性を検出します。例えば、しきい値が「中」の場合、「中」、「高」、「重大」の脆弱性が含まれます。選択した深刻度以上の脆弱性が検出された場合に、パイプラインは失敗します。
ビルドパイプラインでSARIFレポートを生成し、成果物として自動的にアップロードできます。
検出された脆弱性は即座に可視化されるので、Contrast Webインターフェイスで脆弱性の詳細を確認し、修復に役立てることができます。
開始する前に
対応しているOS:
Windows(最新)
Ubuntu(最新)
Mac OS(最新)
Contrast ScanのADOプラグインをインストール
Microsoft AzureのWebサイトにログインします。
Azureポータルにリダイレクトされます。
「Azure DevOps Organizations」を選択します。Create new organizationを選択し、セットアップ手順に従います。
既存の組織を選択することもできます。
組織を選択し、Azure DevOpsポータルを開きます。
拡張機能をインストールします
Contrastを検索し、Contrast ADO Pipeline Integration拡張機能を選択します。Get it freeを選択します。
ご利用の組織にインストールして下さい。
ローカルスキャンエンジンのビルドパイプラインワークフロー
Azure DevOpsポータルで、プロジェクトをAzureリポジトリにクローンします。
左側のパネルでRepos > Filesを選択します。
「Import a repository」でImportを選択します。
「Clone URL」を入力しImportを選択します。
ブランチを作成します。
Branchesを選択し、New branchを選択します。
feature/scan-local-with-sastのような形式で新しいブランチの名前を入力し、Createを選択します。feature/を使用すると、全てのfeatureブランチが1つのフォルダにまとめられます。Contrastのアイテムを全てグループ化すると便利です。例えば、contrast/scan-local-with-sastのようなブランチ名を使用できます。
Contrast接続サービス用のサービス接続を作成します。
Project Settings > Service connections > Create service connectionに進みます。
「New service connection」の一覧から、Contrastを選択し、Nextを選択します。
Contrast Webインターフェイスから必要な情報を入力し、必要に応じてロギング(logging)オプションを有効または無効にします。
サービスキーとAPIキーを見つけるには、Contrast Webインターフェイスのユーザメニューで、 組織の設定 > エージェントキーを選択し、キーを選択したら 従来のエージェントキーを選択します。
ロギングオプションを有効にすると、パイプライン実行時のタスクの結果が記録され、ログファイルに保存されます。ログファイルは、パイプライン成果物として保存されます。この成果物は、コンソールログとは別に保存されます。
新しいビルドパイプラインを作成します。
「Create Pipeline」を選択します。コードがあるAzure Repos Gitを選択します。
作成したプロジェクトを選択し、Starter pipelineを選択します。
右上にあるShow assistantを選択します。
タスク一覧でContrast Local Scannerを検索し、必要な情報を全て入力します。
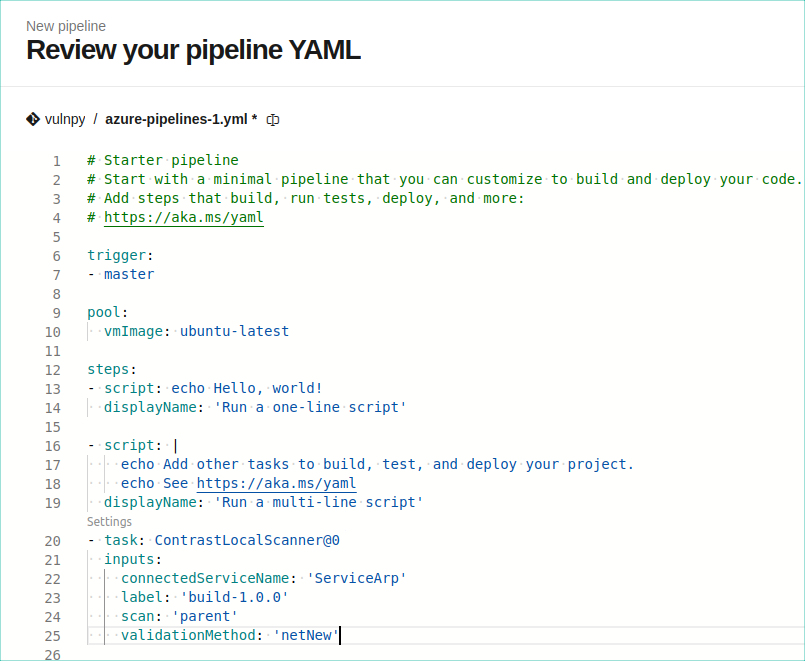
Addを選択したら、タスクがローカルスキャン用に適切に作成されていることを確認します。YAMLファイルは上記の例のようになるはずです。
タスクを作成した後、ブランチにコミットがあれば自動的にビルドが開始されます。ジョブが成功すると、タスクのコンソールログは次の例のようになります。
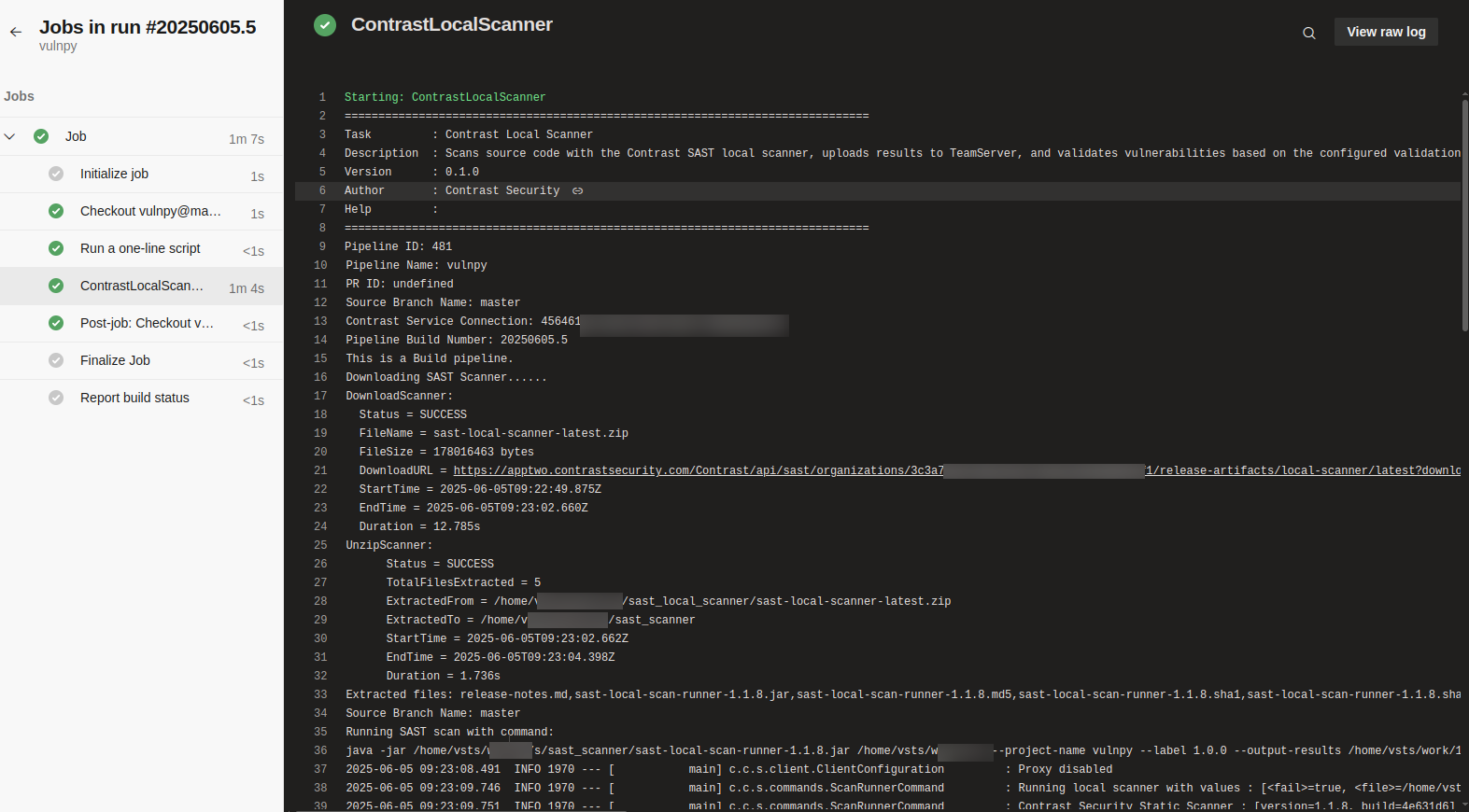
ログには、次の情報が含まれます。
パイプラインID
パイプライン名
プルリクエストID
ソースブランチ名
Contrastサービス接続ID
パイプラインのビルド番号
パイプラインの種類(ビルドまたはリリース)
スキャナのダウンロード状況
スキャナの解凍状況
スキャナの実行状況
エラーメッセージ:ビルドパイプラインが失敗した場合、親ブランチと開発ブランチに対して、Contrast Webインターフェイスのスキャン概要ページへのリンクが表示されます。
ローカルスキャンエンジンのリリースパイプラインワークフロー
Azure DevOpsポータルの左側のパネルで、Pipelines下のReleasesを選択します。
New pipelineを選択します。
アーティファクトを作成します。
Add an artifact選択し、Azure Repo選択します。
パイプラインを実行するプロジェクトを選択し、ブランチを選択します。
Addを選択します。
コードの変更に基づいてパイプラインをトリガーするには、稲妻アイコン(
 )を選択し、Continuous deployment triggerを有効にします。
)を選択し、Continuous deployment triggerを有効にします。ステージを作成します。
Addを選択し、Empty jobを選択します。
ステージ名を入力し、Saveを選択します。
タスクを追加する前に、ホストされるエージェントを設定します。
選択したステージで、Tasksタブを開きます。
Agent jobを選択します。
「Agent selection」にて:
「Agent pool」にAzure Pipelinesを設定します。
利用する要件に合わせて「Agent Specification」を次のいずれかに設定したら、「Save」を選択します。
ubuntu-latestmacos-latestwindows-latest
Contrast Local Scannerタスクをステージに追加します。
Tasksタブを選択します。
「Agent job」の横にある、追加アイコン(
)を選択します。
検索バーにContrast Local Scannerと入力します。
検索結果から、Addを選択して、タスクをステージに含めます。
Contrastサービス接続を選択し、必要なフィールドに情報を入力して、Saveを選択します。
ブランチへのコミットがあれば、パイプラインが開始されて、次の例に示すような結果になります。
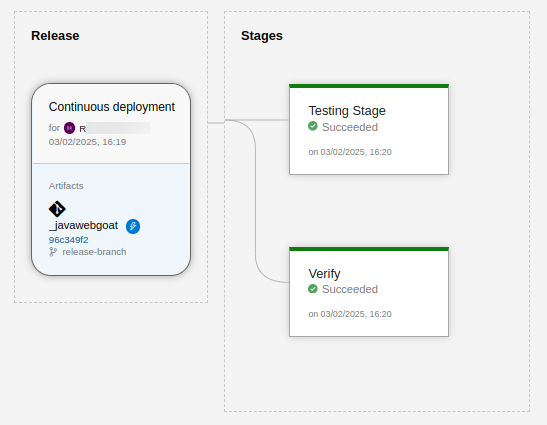
ステージにカーソルを合わせ、Logsアイコンを選択するとログが表示されます。
Contrast Scanローカル エンジンのADOログを検索
DevOpsポータルで、プロジェクトに移動します。
Pipelines > Releasesを選択します。
ログファイルを参照したいリリースを開きます。
ステージにカーソルを合わせ、 Logs(ログ)を選択します。
Download all logsを選択します。
注記
リリースパイプラインからresults.sarif.jsonファイル(スキャン結果)をダウンロードすることはできません。